rfid tags complete silent mode RFIDsec offers a complete solution which comprises a RFID tag, software which uses essential security and web-services, that ensure an authenticity check for the consumer and recognising whether the chip is genuine or a clone. The chip is unique as it can enter into a “silent mode”, for example when a customer leaves the store. The Nexus 6P feels solid, whole, and balanced. The glass on the front symmetrically frames the 5.7-inch screen with dual speakers and a blessed lack of logos. And heck, if you want, you can turn .
0 · tuning rfid settings
1 · tuning rfid configuration in session
2 · session 0 rfid
3 · rfid settings explained
4 · rfid session settings
Step 2: Tap New Automation or + (from the top-right corner). Step 3: Here, scroll down or search for NFC. Tap it. Step 4: Tap Scan. Hold your device over an NFC tag/sticker. .Posted on Nov 1, 2021 12:10 PM. On your iPhone, open the Shortcuts app. Tap on the Automation tab at the bottom of your screen. Tap on Create Personal Automation. Scroll down and select NFC. Tap on Scan. Put your iPhone near the NFC tag. Enter a name for your tag. .
RFIDsec has announced the availability of the first series of RFID solutions to completely block unauthorized access to a tag. Alongside with uncontested security, the RFIDsec solutions offer owners the possibility of differentiated access using a patent pending and secure access .

RFIDsec offers a complete solution which comprises a RFID tag, software which uses essential security and web-services, that ensure an authenticity check for the consumer and recognising .RFIDsec has announced the availability of the first series of RFID solutions to completely block unauthorized access to a tag. Alongside with uncontested security, the RFIDsec solutions offer owners the possibility of differentiated access using a patent pending and secure access management system.RFIDsec offers a complete solution which comprises a RFID tag, software which uses essential security and web-services, that ensure an authenticity check for the consumer and recognising whether the chip is genuine or a clone. The chip is unique as it can enter into a “silent mode”, for example when a customer leaves the store. Radio Frequency Identification (RFID) technology uses radio waves to identify virtually anything. It is a wireless system consisting of an RFID tag and an RFID reader. RFID tags store data that can be read, even from a distance—without making any physical contact or requiring a line of sight.
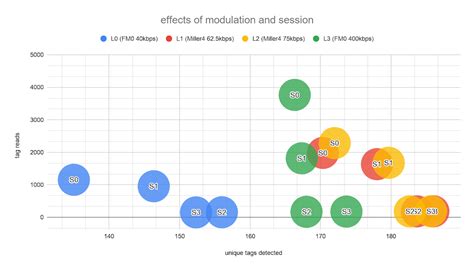
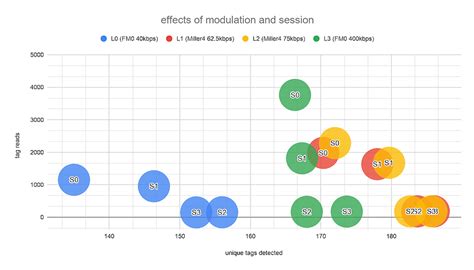
With session 2 or 3 after the tags are read, they remain silent for at least two seconds after the reader stops transmitting, allowing other, weaker tags to be heard. Summary The number of RFID configurations can be bewildering, but the following guidelines will get your application going in the right direction:After touching it with an iPhone, the phone will automatically switch to silent mode, turn off unnecessary notifications, and open commonly used office software. Information transmission: NFC tags can also be used to transmit information such as text and URLs.
A system developed by Friendly Technologies uses the privacy mode found in NXP's Icode and Ucode chips to keep tags from being read by unauthorized parties.Understanding the different modes in the ISO/IEC 18000-3 standard is critical for selecting the right RFID solution for your needs. While Mode 1 offers low-cost, multi-tag solutions, Mode 3 leans towards high-security and robust data transmission, with Mode 2 filling a niche in between.
Active RFID tags, distinguished by their internal power source, operate using a battery to actively transmit signals to RFID readers. The inclusion of a power source empowers active tags to broadcast signals over longer distances, enabling read ranges that can extend up to hundreds of meters.
Discover the essentials of RFID Tags, including their types, working principles, benefits, and selection tips. Get expert guidance on choosing the right RFID tags for your needs with SAG.The "silent mode" is considered as an alternative to kill the tag. In this mode, the RFID tag can be shut off instead of killing it at the time the customer purchases an item. This mode maintains all the information that could be utilized further in case of reclamation situations.RFIDsec has announced the availability of the first series of RFID solutions to completely block unauthorized access to a tag. Alongside with uncontested security, the RFIDsec solutions offer owners the possibility of differentiated access using a patent pending and secure access management system.
RFIDsec offers a complete solution which comprises a RFID tag, software which uses essential security and web-services, that ensure an authenticity check for the consumer and recognising whether the chip is genuine or a clone. The chip is unique as it can enter into a “silent mode”, for example when a customer leaves the store. Radio Frequency Identification (RFID) technology uses radio waves to identify virtually anything. It is a wireless system consisting of an RFID tag and an RFID reader. RFID tags store data that can be read, even from a distance—without making any physical contact or requiring a line of sight. With session 2 or 3 after the tags are read, they remain silent for at least two seconds after the reader stops transmitting, allowing other, weaker tags to be heard. Summary The number of RFID configurations can be bewildering, but the following guidelines will get your application going in the right direction:After touching it with an iPhone, the phone will automatically switch to silent mode, turn off unnecessary notifications, and open commonly used office software. Information transmission: NFC tags can also be used to transmit information such as text and URLs.
A system developed by Friendly Technologies uses the privacy mode found in NXP's Icode and Ucode chips to keep tags from being read by unauthorized parties.Understanding the different modes in the ISO/IEC 18000-3 standard is critical for selecting the right RFID solution for your needs. While Mode 1 offers low-cost, multi-tag solutions, Mode 3 leans towards high-security and robust data transmission, with Mode 2 filling a niche in between. Active RFID tags, distinguished by their internal power source, operate using a battery to actively transmit signals to RFID readers. The inclusion of a power source empowers active tags to broadcast signals over longer distances, enabling read ranges that can extend up to hundreds of meters. Discover the essentials of RFID Tags, including their types, working principles, benefits, and selection tips. Get expert guidance on choosing the right RFID tags for your needs with SAG.
tuning rfid settings
micro epoxy nfc metro tag

Mar 14, 2016
rfid tags complete silent mode|tuning rfid settings