card reader looks like a phone access control General RFID cards, and more particularly NFC cards are used very commonly in access control and mobile payment, the latter primarily in transit cards and bank cards. In this section, we’ll review how those work, and which cards you might find yourself using. See more Are you sure it is an iPhone X? Go to Settings > General > About > Model .
0 · magnetic access card reader
1 · access control card readers
2 · access control card reader types
3 · access card reader types
Hold your phone close to the Apple Pay or NFC symbol on the card reader until you see the word Done appear at the bottom of the screen beneath a blue checkmark in a circle. If you want to use a different card from the default, tap the image of the card when it appears and select another card before holding the phone up to the card reader. .
Before we dive into the different varieties of cards out there, we should discuss what the tech is behind access cards — how do they actually communicate with the smart readers you have at . See more
With so many different kinds of access cards out there, it can be difficult to know which one you have, or whether yours is secure, or even if you need it anymore. Hopefully, this article . See moreGeneral RFID cards, and more particularly NFC cards are used very commonly in access control and mobile payment, the latter primarily in transit cards and bank cards. In this section, we’ll review how those work, and which cards you might find yourself using. See more
Selecting the right access control card reader depends on your facility's security needs, .
2-in-1 mobile credential and prox card reader that easily replaces wired access card readers. . Simply put, an access control card reader is a security system that requires a card to be swiped or tapped to verify the credentials of the person using it to gain access. Most access control card readers emit a signal that .General RFID cards, and more particularly NFC cards are used very commonly in access control and mobile payment, the latter primarily in transit cards and bank cards. In this section, we’ll review how those work, and which cards you might find yourself using.Selecting the right access control card reader depends on your facility's security needs, budget, and user convenience. Whether you opt for the simplicity of a magnetic stripe reader or the advanced features of a biometric or mobile credential reader, each type of card reader offers unique benefits.
2-in-1 mobile credential and prox card reader that easily replaces wired access card readers. This mobile reader supports most smartphones and connects directly to new or existing wired access control panel.Simply put, an access control card reader is a security system that requires a card to be swiped or tapped to verify the credentials of the person using it to gain access. Most access control card readers emit a signal that reads the data stored on a card.
This article serves as an exhaustive guide for security installers looking to gain insights into the variety of access control card readers available today. We’ll explore the technology behind these devices, their advantages, and disadvantages, and how they fit into different security ecosystems.
magnetic access card reader
access control card readers
smart card authentication step-by-step
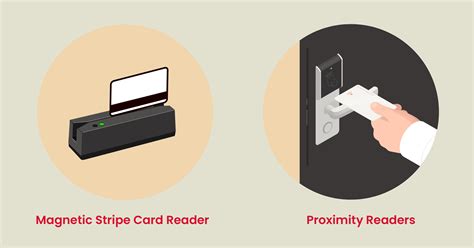
1. Key Card Readers. Key card readers are one of the most common types of access control readers. When a card is registered, access is granted. A good access control system using key cards will maintain a database of key cards for a log history and will allow you to manage access as needed to update, add, or remove access for specific cards.With access control with a card reader, an employee, visitor, or guest uses a digital access card as a key. This card is linked to a unique person's details (name, role, position). The access control system administrator determines who receives a card and issues it.Card Readers. Many businesses utilize card readers as their primary form of access control. Card readers use key cards instead of physical keys or codes to allow entry. Generally, there are two types of access control key card readers — proximity and magnetic.
BlueDiamond™ multi-technology readers are among the most versatile access control readers on the market, work seamlessly with existing infrastructure and leverage open credentialing standards. The readers are non-proprietary, access control platform agnostic and support the standard output protocols including Supervised F/2F (SF/2F), Wiegand .Access readers by SimpleAccess offer options to work with smartphones, mobile devices, pin codes, fobs, and/or access cards. Whether installing a new system or upgrading an existing system, our wired and wireless options provide flexible and lower-cost access reader solutions.General RFID cards, and more particularly NFC cards are used very commonly in access control and mobile payment, the latter primarily in transit cards and bank cards. In this section, we’ll review how those work, and which cards you might find yourself using.
Selecting the right access control card reader depends on your facility's security needs, budget, and user convenience. Whether you opt for the simplicity of a magnetic stripe reader or the advanced features of a biometric or mobile credential reader, each type of card reader offers unique benefits.2-in-1 mobile credential and prox card reader that easily replaces wired access card readers. This mobile reader supports most smartphones and connects directly to new or existing wired access control panel.
Simply put, an access control card reader is a security system that requires a card to be swiped or tapped to verify the credentials of the person using it to gain access. Most access control card readers emit a signal that reads the data stored on a card.
This article serves as an exhaustive guide for security installers looking to gain insights into the variety of access control card readers available today. We’ll explore the technology behind these devices, their advantages, and disadvantages, and how they fit into different security ecosystems. 1. Key Card Readers. Key card readers are one of the most common types of access control readers. When a card is registered, access is granted. A good access control system using key cards will maintain a database of key cards for a log history and will allow you to manage access as needed to update, add, or remove access for specific cards.With access control with a card reader, an employee, visitor, or guest uses a digital access card as a key. This card is linked to a unique person's details (name, role, position). The access control system administrator determines who receives a card and issues it.
Card Readers. Many businesses utilize card readers as their primary form of access control. Card readers use key cards instead of physical keys or codes to allow entry. Generally, there are two types of access control key card readers — proximity and magnetic.BlueDiamond™ multi-technology readers are among the most versatile access control readers on the market, work seamlessly with existing infrastructure and leverage open credentialing standards. The readers are non-proprietary, access control platform agnostic and support the standard output protocols including Supervised F/2F (SF/2F), Wiegand .
seva sindhu smart card application
access control card reader types
You can use contactless (card or device) or an Oyster card to pay as you go on bus, .
card reader looks like a phone access control|access card reader types