mifare card commands This card selection process (card activation) is described in the ISO14443-3 for contactless proximity systems. The dramatic increase in contactless applications has made the correct . Try the Tag Reader in Control Center. If your iPhone isn’t automatically recognizing NFC tags, you can try using the NFC Tag Reader tool that’s built into your iPhone. However, this is only .
0 · MIFARE ev3 type identification
1 · MIFARE desfire type identification
2 · MIFARE desfire ev3 identification
3 · MIFARE cpt codes
A quick point of clarity to hopefully help you avoid some confusion— the YubiKey NEO was its own series and actually predates the YubiKey 4 series. And yeah technically, but idk how expensive HID NFC readers are. Unless you REALLY .
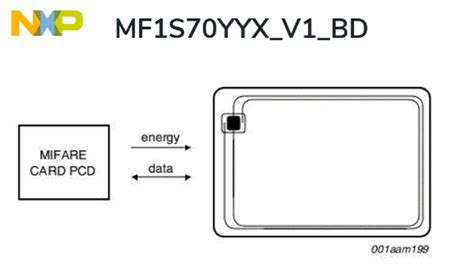
The MIFARE Classic card activation follows the ISO/IEC 14443 Type A. After the MIFARE Classic card has been selected, it can either be deactivated using the ISO/IEC 14443 Halt command, .This document provides an easy guideline how the ISO/IEC 14443 compatible PCD should handle the MIFARE cards and how it can distinguish between the different available types of MIFARE .This card selection process (card activation) is described in the ISO14443-3 for contactless proximity systems. The dramatic increase in contactless applications has made the correct .This list gives an overview of the existing commands that can be used with any transponder that is based on ISO14443A, including all MiFare dialects. Any commands that are specific to a .
This is a sample app to demonstrate how to work with a Mifare DESFire EV1/EV2/EV3 card. For simplicity this app uses a DESFire tag with factory settings means: it uses Plain . DOWNLOAD AND READ THE DOCUMENTATIONS. First thing to do is to obtain the documentation of the card from the manufacturer (NXP in this case) and the Prox’N’Roll .
Change Key (45h) . This command allows to change any key stored on the PICC. If AID=0x00 is selected, the change applies to the PICC master key and therefore only KeyNo = 0x00 is valid .This command manages MIFARE authentication to enable a secure communication to any MIFARE Mini, MIFARE 1K and MIFARE 4K card. The authentication is described in the . Commands needed to clone a Mifare Classic 1k card using the Proxmark 3, some lessons I learned along the wayThe MIFARE® Classic family is the most widely used contactless smart card ICs operating in the 13.56 MHz fre-quency range with read/write capability and ISO/IEC 14443 A compliance. Smart cards based on MIFARE® Classic ICs are a commonly known solution in various applications such as: Access Control Public Transportation Electronic Toll Collection
The MIFARE Classic card activation follows the ISO/IEC 14443 Type A. After the MIFARE Classic card has been selected, it can either be deactivated using the ISO/IEC 14443 Halt command, or the MIFARE Classic commands can be performed.
MIFARE ev3 type identification
This document provides an easy guideline how the ISO/IEC 14443 compatible PCD should handle the MIFARE cards and how it can distinguish between the different available types of MIFARE cards.This card selection process (card activation) is described in the ISO14443-3 for contactless proximity systems. The dramatic increase in contactless applications has made the correct selection of one single contactless card out of a possible number of cards in the reader field become more important.This list gives an overview of the existing commands that can be used with any transponder that is based on ISO14443A, including all MiFare dialects. Any commands that are specific to a certain type of MiFare-Type can be found in the next chapter.This is a sample app to demonstrate how to work with a Mifare DESFire EV1/EV2/EV3 card. For simplicity this app uses a DESFire tag with factory settings means: it uses Plain communication only (no MACed or Enciphered Communication)
DOWNLOAD AND READ THE DOCUMENTATIONS. First thing to do is to obtain the documentation of the card from the manufacturer (NXP in this case) and the Prox’N’Roll developer’s reference manual. From the card’s functional specifications, we can see that the memory is structured in 16 pages of 4 bytes. The four first pages (0-3) contain .
Change Key (45h) . This command allows to change any key stored on the PICC. If AID=0x00 is selected, the change applies to the PICC master key and therefore only KeyNo = 0x00 is valid (only one PICC master key is present on a PICC).
This command manages MIFARE authentication to enable a secure communication to any MIFARE Mini, MIFARE 1K and MIFARE 4K card. The authentication is described in the MFRC522 datasheet section 10.3.1.9 and http:// www.nxp.com/documents/data_sheet/MF1S503x.pdf section 10.1. for use with MIFARE Classic PICCs.
MIFARE desfire type identification
MIFARE desfire ev3 identification
MIFARE cpt codes
Commands needed to clone a Mifare Classic 1k card using the Proxmark 3, some lessons I learned along the wayThe MIFARE® Classic family is the most widely used contactless smart card ICs operating in the 13.56 MHz fre-quency range with read/write capability and ISO/IEC 14443 A compliance. Smart cards based on MIFARE® Classic ICs are a commonly known solution in various applications such as: Access Control Public Transportation Electronic Toll Collection
The MIFARE Classic card activation follows the ISO/IEC 14443 Type A. After the MIFARE Classic card has been selected, it can either be deactivated using the ISO/IEC 14443 Halt command, or the MIFARE Classic commands can be performed.
This document provides an easy guideline how the ISO/IEC 14443 compatible PCD should handle the MIFARE cards and how it can distinguish between the different available types of MIFARE cards.
This card selection process (card activation) is described in the ISO14443-3 for contactless proximity systems. The dramatic increase in contactless applications has made the correct selection of one single contactless card out of a possible number of cards in the reader field become more important.This list gives an overview of the existing commands that can be used with any transponder that is based on ISO14443A, including all MiFare dialects. Any commands that are specific to a certain type of MiFare-Type can be found in the next chapter.This is a sample app to demonstrate how to work with a Mifare DESFire EV1/EV2/EV3 card. For simplicity this app uses a DESFire tag with factory settings means: it uses Plain communication only (no MACed or Enciphered Communication)
DOWNLOAD AND READ THE DOCUMENTATIONS. First thing to do is to obtain the documentation of the card from the manufacturer (NXP in this case) and the Prox’N’Roll developer’s reference manual. From the card’s functional specifications, we can see that the memory is structured in 16 pages of 4 bytes. The four first pages (0-3) contain .Change Key (45h) . This command allows to change any key stored on the PICC. If AID=0x00 is selected, the change applies to the PICC master key and therefore only KeyNo = 0x00 is valid (only one PICC master key is present on a PICC).This command manages MIFARE authentication to enable a secure communication to any MIFARE Mini, MIFARE 1K and MIFARE 4K card. The authentication is described in the MFRC522 datasheet section 10.3.1.9 and http:// www.nxp.com/documents/data_sheet/MF1S503x.pdf section 10.1. for use with MIFARE Classic PICCs.
nfc tag nexus 6p app
nfc tag programming windows
Yes, but with limitations. Smartphones can read some RFID tags, but they are mainly limited to .
mifare card commands|MIFARE cpt codes