rfid attack methods tracking There are several ways in which RFID hacking can occur: Eavesdropping: Attackers intercept and decode the radio signals exchanged between the tags and readers, gaining unauthorized access to sensitive information. RFID Cloning: Hackers clone legitimate RFID tags and use them to gain unauthorized access to restricted areas or valuable assets. A common misconception is that NFC operations are tied to the mobile network services facilitated by the SIM. However, it is crucial to delineate the functions of NFC that are independent of a SIM card. NFC technology is .
0 · sniffing rfid
1 · rfid tracking
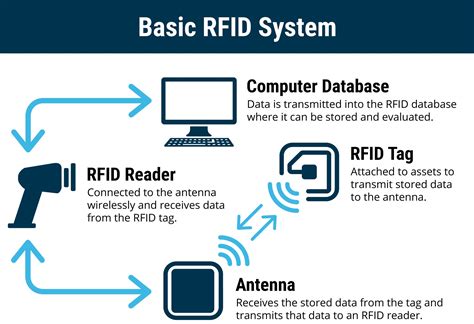
2 · rfid systems
3 · rfid security threats
4 · rfid security problems
5 · rfid hacking protection
6 · rfid hacking examples
7 · rfid hacking definition
Kia Access App. Charging with the Kia Access App: The Kia Access App can help you find the nearest charging station, and also displays charging status and Scheduled Charging .
The most common techniques include: Active Jamming. RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos by blocking access with ID cards. .There are several ways in which RFID hacking can occur: Eavesdropping: Attackers intercept .
The most common techniques include: Active Jamming. RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos .There are several ways in which RFID hacking can occur: Eavesdropping: Attackers intercept and decode the radio signals exchanged between the tags and readers, gaining unauthorized access to sensitive information. RFID Cloning: Hackers clone legitimate RFID tags and use them to gain unauthorized access to restricted areas or valuable assets.
By reading information received from RFID tag an attacker can track the location and movement of an object or a person. When a tag is attached to an object and the object enter the RFID reader’s field, the RFID read can identify the object and locate its position.A common way to defeat a spoofing attack is to implement an RFID authentication protocol and data encryption, which increases the cost and technology complexity needed for a successful attack.While RFID technology has many benefits, such as asset tracking and supply chain management, it also presents vulnerabilities that malicious actors can exploit. This article will explore the basics of RFID technology, the potential threats posed by RFID attacks, and the best practices for protecting against them. Below are 7 known security attacks hackers can perform on an RFID system. 1. Reverse Engineering. Like most products, RFID tags and readers can be reverse engineered; however, it would take a lot of knowledge about the protocols and features to be successful.
RFID technology is the core technology of the perception layer of the Internet of Things, which can realize the real-time transmission of information between ob.
In this paper we analyze some of the most common types of attack on RFID tags: unauthorized disabling, unauthorized cloning, unauthorized tracking, and response replay. We introduce security mechanisms appropriate to defeat these attacks, and show how a recently proposed RFID authentication protocol uses them to achieve security.
This study provides an overview of RFID technology. This study aims to identify potential vulnerabilities in RFID-related physical controls in an infrastructure. This includes evaluating the effectiveness of encryption algorithms, frequency range and band, and RFID type. 1 Introduction. RFID is expected to be the basic technology for ubiquitous network or computing, and to be associated with other technology such as telemetric, and wireless sensors. Recently, the wide deployment of RFID systems in a variety of applications has raised many concerns about the privacy and the security issues. The most common techniques include: Active Jamming. RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos .There are several ways in which RFID hacking can occur: Eavesdropping: Attackers intercept and decode the radio signals exchanged between the tags and readers, gaining unauthorized access to sensitive information. RFID Cloning: Hackers clone legitimate RFID tags and use them to gain unauthorized access to restricted areas or valuable assets.
By reading information received from RFID tag an attacker can track the location and movement of an object or a person. When a tag is attached to an object and the object enter the RFID reader’s field, the RFID read can identify the object and locate its position.A common way to defeat a spoofing attack is to implement an RFID authentication protocol and data encryption, which increases the cost and technology complexity needed for a successful attack.While RFID technology has many benefits, such as asset tracking and supply chain management, it also presents vulnerabilities that malicious actors can exploit. This article will explore the basics of RFID technology, the potential threats posed by RFID attacks, and the best practices for protecting against them. Below are 7 known security attacks hackers can perform on an RFID system. 1. Reverse Engineering. Like most products, RFID tags and readers can be reverse engineered; however, it would take a lot of knowledge about the protocols and features to be successful.
RFID technology is the core technology of the perception layer of the Internet of Things, which can realize the real-time transmission of information between ob.In this paper we analyze some of the most common types of attack on RFID tags: unauthorized disabling, unauthorized cloning, unauthorized tracking, and response replay. We introduce security mechanisms appropriate to defeat these attacks, and show how a recently proposed RFID authentication protocol uses them to achieve security. This study provides an overview of RFID technology. This study aims to identify potential vulnerabilities in RFID-related physical controls in an infrastructure. This includes evaluating the effectiveness of encryption algorithms, frequency range and band, and RFID type.

sniffing rfid
rfid tracking

rfid systems
rfid security threats
rfid security problems
Custom Animal Crossing Amiibo Cards. ALL Series are Available in our store. Fast Ship from United States. All orders will be shipped in 1 business day. 30 Days Money Back Guarantee. Sales Promotion up to 30% Off Discount. All .
rfid attack methods tracking|rfid tracking