smart card logon and pki This 101 covers PIV credential basics, including: What PIV is, contains, and looks like. The .
Run Skylanders GUI Tool. Open the Skylanders GUI Tool folder and go to this .
0 · smart card two factor authentication
1 · smart card computer access
2 · smart card authentication step by
3 · pki smarttoken
4 · pki smart card authentication
5 · fips 140 2 smart card
6 · authentication smart card
7 · adfs smart card authentication
Android offers unique advantages for reading NFC tags compared to other mobile operating systems: Widespread NFC hardware support – Most modern Android devices contain NFC radios that can read tags. Flexible .
These Windows Domain configuration guides will help you configure your Windows network .Enablement of mandatory smart card login for all Mac workstations and laptops within your e.
You can enable a smart card logon process with Microsoft Windows 2000 and a .

MSFT smart card authentication is listed in PKINIT RFC 4556 however I don't see any OIDs . To integrate smart cards with Entra ID or Active Directory, organizations need to .
This 101 covers PIV credential basics, including: What PIV is, contains, and looks like. The . This article for IT professionals and smart card developers describes the Group .
smart card two factor authentication
This is my first blog and today I’ll share with you how to configure a Hyper-V .

Enablement of mandatory smart card login for all Mac workstations and laptops within your .Refer to the relevant smart card logon guide available from the DoD PKE site under For .
These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details on configurations and using generic smart cards.
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
smart card computer access
You can enable a smart card logon process with Microsoft Windows 2000 and a non-Microsoft certification authority (CA) by following the guidelines in this article. Limited support for this configuration is described later in this article.
MSFT smart card authentication is listed in PKINIT RFC 4556 however I don't see any OIDs listed. Based on this and this KB article the EKU section of the certificate should contain "Client Authentication" or "Microsoft smart card".To integrate smart cards with Entra ID or Active Directory, organizations need to integrate a Public-Key Infrastructure (PKI) with their solutions. SecureW2’s cloud-based managed PKI integrates directly with Microsoft identities and offers a client that can directly issue certificates on Smart Cards like YubiKeys.
This 101 covers PIV credential basics, including: What PIV is, contains, and looks like. The basics of getting started with PIV credentials. Implementation practices for using PIV for network authentication (smart card logon) are found under implementations. Who is eligible for a . This article for IT professionals and smart card developers describes the Group Policy settings, registry key settings, local security policy settings, and credential delegation policy settings that are available for configuring smart cards.
This is my first blog and today I’ll share with you how to configure a Hyper-V environment in order to enable virtual smart card logon to VM guests by leveraging a new Windows 10 feature: virtual Trusted Platform Module (TPM).Enablement of mandatory smart card login for all Mac workstations and laptops within your environment will help align to the NIST SP 800-53 Identification and Authentication family of controls to support FISMA compliance.
Refer to the relevant smart card logon guide available from the DoD PKE site under For Administrators, Integrators, and Developers > Network Configuration for detailed instructions.These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details on configurations and using generic smart cards.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. You can enable a smart card logon process with Microsoft Windows 2000 and a non-Microsoft certification authority (CA) by following the guidelines in this article. Limited support for this configuration is described later in this article.
smart card authentication step by
MSFT smart card authentication is listed in PKINIT RFC 4556 however I don't see any OIDs listed. Based on this and this KB article the EKU section of the certificate should contain "Client Authentication" or "Microsoft smart card".To integrate smart cards with Entra ID or Active Directory, organizations need to integrate a Public-Key Infrastructure (PKI) with their solutions. SecureW2’s cloud-based managed PKI integrates directly with Microsoft identities and offers a client that can directly issue certificates on Smart Cards like YubiKeys.
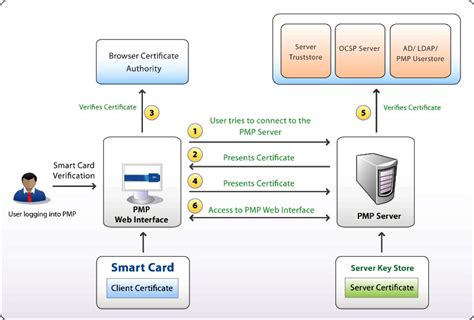
This 101 covers PIV credential basics, including: What PIV is, contains, and looks like. The basics of getting started with PIV credentials. Implementation practices for using PIV for network authentication (smart card logon) are found under implementations. Who is eligible for a . This article for IT professionals and smart card developers describes the Group Policy settings, registry key settings, local security policy settings, and credential delegation policy settings that are available for configuring smart cards. This is my first blog and today I’ll share with you how to configure a Hyper-V environment in order to enable virtual smart card logon to VM guests by leveraging a new Windows 10 feature: virtual Trusted Platform Module (TPM).Enablement of mandatory smart card login for all Mac workstations and laptops within your environment will help align to the NIST SP 800-53 Identification and Authentication family of controls to support FISMA compliance.
em4200 rfid card price
explain rfid tags
Save and categorize content based on your preferences. Near Field Communication (NFC) is a set of short-range wireless technologies, typically requiring a distance of 4 cm or .
smart card logon and pki|pki smart card authentication