are rfid tags secure Some people are concerned that attackers could use a handheld device in a crowd to read RFID information from nearby credit cards with contactless payment information embedded in them. Identity thieves could read the same information from an RFID . See more Supermarket alarm mystery. red0209 Posts: 125 Forumite. 11 July 2015 at .
0 · two types of rfid tags
1 · rfid tags and their uses
2 · rfid radio frequency identification tags
3 · rfid privacy and security issues
4 · retail anti theft security tags
5 · radio frequency identification tags are
6 · problems with rfid technology
7 · problems with rfid
1. Read and save the card with your Flipper Zero. 2. Go to Main Menu -> NFC -> Saved -> Name of the saved card -> Extract MF Keys. Flipper Zero will emulate this card for the MFKey32 attack. Your Flipper Zero is ready to collect the .Pro-Tip #3 – NFC does more than just load PRESTO funds and passes instantly. With NFC functionality, you can also now easily check your real-time transaction history, card balance and last time you’ve tapped on or off by using the ‘Check Balance’ feature and holding .
RFID stands for radio-frequency identification. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a battery, but many RFID tags . See more
RFID tags can replace bar codes and QR codes. A bar code can only be read if the reader can visually see the bar code. RFID tags can be read if the reader is nearby, even if a bar code . See more
two types of rfid tags
rfid tags and their uses
Some people are concerned that attackers could use a handheld device in a crowd to read RFID information from nearby credit cards with contactless payment information embedded in them. Identity thieves could read the same information from an RFID . See more A simple introduction to how RF and RFID tags are used in smart cards, toll collection, shop security, and other everyday applications. RFID tags can be used for tracking packages in the mail or goods in a warehouse. The RFID tag can contain tracking information or just a unique identification code. Modern passports in many countries -- including the USA and Canada -- also contain an RFID chip. A simple introduction to how RF and RFID tags are used in smart cards, toll collection, shop security, and other everyday applications.
Your security needs may vary, depending on the purpose your RFID system serves. However, ensuring that only you and your trusted partners can access your data will increase the value of your RFID solution dramatically. Security Risks. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data.RFID attacks occur when an unauthorized individual intercepts or manipulates the signals transmitted between RFID tags and readers. There are several techniques commonly used by attackers to exploit RFID vulnerabilities.This post aims to highlight several important RFID related security issues. RFID Counterfeiting: depending on the computing power, RFID can be classified into three categories: Basic tags; Tags that uses symmetric keys; Tags that uses public-key; Since basic tags do not use any encryption, they can be counterfeited easily.
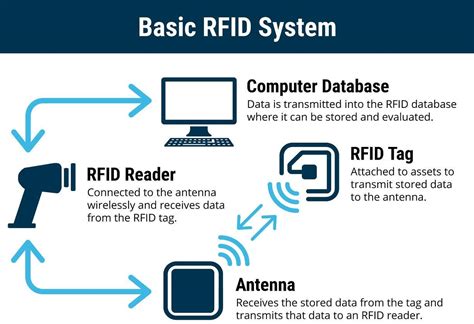
Eavesdropping is a significant security risk associated with RFID technology, where unauthorized individuals intercept and monitor the communication between RFID tags and readers. By capturing and analyzing the transmitted data, attackers can gain access to sensitive information or track the movements of tagged items without detection. It is recommended for RFID users to take steps to secure their data by locking memory banks. Middleware should also be used to prevent man-in-the-middle attacks—where fraudsters place a device between the RFID tag and the reader to .Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder called a tag, a radio receiver, and a transmitter.
This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks. RFID tags can be used for tracking packages in the mail or goods in a warehouse. The RFID tag can contain tracking information or just a unique identification code. Modern passports in many countries -- including the USA and Canada -- also contain an RFID chip. A simple introduction to how RF and RFID tags are used in smart cards, toll collection, shop security, and other everyday applications.
Your security needs may vary, depending on the purpose your RFID system serves. However, ensuring that only you and your trusted partners can access your data will increase the value of your RFID solution dramatically. Security Risks. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data.RFID attacks occur when an unauthorized individual intercepts or manipulates the signals transmitted between RFID tags and readers. There are several techniques commonly used by attackers to exploit RFID vulnerabilities.This post aims to highlight several important RFID related security issues. RFID Counterfeiting: depending on the computing power, RFID can be classified into three categories: Basic tags; Tags that uses symmetric keys; Tags that uses public-key; Since basic tags do not use any encryption, they can be counterfeited easily.
rfid radio frequency identification tags
Eavesdropping is a significant security risk associated with RFID technology, where unauthorized individuals intercept and monitor the communication between RFID tags and readers. By capturing and analyzing the transmitted data, attackers can gain access to sensitive information or track the movements of tagged items without detection. It is recommended for RFID users to take steps to secure their data by locking memory banks. Middleware should also be used to prevent man-in-the-middle attacks—where fraudsters place a device between the RFID tag and the reader to .Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder called a tag, a radio receiver, and a transmitter.


rfid privacy and security issues
retail anti theft security tags
radio frequency identification tags are
problems with rfid technology
Candidates can check the latest Nuclear Fuel Complex (NFC) Recruitment 2024 ITI Trade Apprentice Vacancy 2024 details and apply online at the www.nfc.gov.in recruitment .
are rfid tags secure|radio frequency identification tags are