cisco ise smart card authentication The purpose of this document is to demonstrate how ISE authenticate / authorize a user that uses a smart card (PIN + Certificate) and password mechanism to login their system. . When you interact with our mobile applications or online services, we and .
0 · Cisco ise certificate signing
1 · Cisco ise certificate authentication
2 · Cisco ise certificate
3 · Cisco ise authentication settings
4 · Cisco ise authentication protocol
5 · Cisco ise authentication policy
6 · Cisco ise authentication example
7 · Cisco ise authentication error
Redstone Federal Credit Union Promotions. $500. Personal Checking Account - $500 Bonus. Open a new qualifying personal checking account. Use promo code MBR500 at account .
This document describes how to configure Client Certificate-based authentication for Identity Services Engine (ISE) management access. In this example, the ISE administrator authenticates against the User certificate to gain Admin access to the Cisco Identity Services Engine (ISE) management GUI. See moreVerify access to the ISE GUI after the Application Server service status changes to running. Super Admin User: Verify that the . See moreUse this section to configure the Client certificate or Smart Card as an external identity for administrative access to the Cisco ISE . See more The purpose of this document is to demonstrate how ISE authenticate / authorize a user that uses a smart card (PIN + Certificate) and password mechanism to login their system. .
This document describes initial configuration to introduce Extensible Authentication Protocol-Transport Layer Security Authentication with Cisco ISE.
With Cisco ISE 1.2 is it possible to enable 802.1x machine AND user smart card authentication simultaneously for wired/wireless clients (specifically Windows 7/8, but Linux or .
Authentication of user using Smart card is done using authentication policy. If you want to authorize them based on AD attribute, then you need to do it in authorization policy .
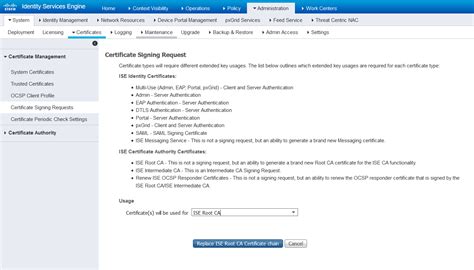
Cisco ISE Configuration. I’m using the Default Network Access allowed protocols but you can easily set it to just the protocols you require (recommended). In the default .This document describes how to configure Client Certificate-based authentication for Identity Services Engine (ISE) management access. In this example, the ISE administrator .
Has anyone gotten smartcard authentication working for ISE GUI admins? I've configured this based on the Cisco documentation and the browser prompts the user to select the certificate . Cisco ISE - Configuring TACACS+ Authentication for Device Administration. Introduction. Centralizing control over network device access using the TACACS+ protocol .
editor shows a smart card (PIN+ Certificate) based authentication for user and machine. EAP-FAST is the EAP method and EAP-TLS is to authenticate using certificate as inner method .
This document describes how to configure Client Certificate-based authentication for Identity Services Engine (ISE) management access. In this example, the ISE administrator authenticates against the User certificate to gain Admin access to the Cisco Identity Services Engine (ISE) management GUI. The purpose of this document is to demonstrate how ISE authenticate / authorize a user that uses a smart card (PIN + Certificate) and password mechanism to login their system. This document describes the components used for this setup, configuration. This document describes initial configuration to introduce Extensible Authentication Protocol-Transport Layer Security Authentication with Cisco ISE.
With Cisco ISE 1.2 is it possible to enable 802.1x machine AND user smart card authentication simultaneously for wired/wireless clients (specifically Windows 7/8, but Linux or OSX would also be good). Authentication of user using Smart card is done using authentication policy. If you want to authorize them based on AD attribute, then you need to do it in authorization policy mapping to a Shell profile/command sets. Cisco ISE Configuration. I’m using the Default Network Access allowed protocols but you can easily set it to just the protocols you require (recommended). In the default protocols, I’m enabling TEAP and EAP Chaining. Modifying the Default Network Access policy under Allowed Protocols.
This document describes how to configure Client Certificate-based authentication for Identity Services Engine (ISE) management access. In this example, the ISE administrator authenticates against the User certificate to gain Admin accessto the Cisco Identity Services Engine (ISE) management GUI. Has anyone gotten smartcard authentication working for ISE GUI admins? I've configured this based on the Cisco documentation and the browser prompts the user to select the certificate and then enter their PIN. Cisco ISE - Configuring TACACS+ Authentication for Device Administration. Introduction. Centralizing control over network device access using the TACACS+ protocol has been the golden standard for many years in most bigger networks because it enables detailed and granular permissions down at the very command level.editor shows a smart card (PIN+ Certificate) based authentication for user and machine. EAP-FAST is the EAP method and EAP-TLS is to authenticate using certificate as inner method based on credential
This document describes how to configure Client Certificate-based authentication for Identity Services Engine (ISE) management access. In this example, the ISE administrator authenticates against the User certificate to gain Admin access to the Cisco Identity Services Engine (ISE) management GUI. The purpose of this document is to demonstrate how ISE authenticate / authorize a user that uses a smart card (PIN + Certificate) and password mechanism to login their system. This document describes the components used for this setup, configuration. This document describes initial configuration to introduce Extensible Authentication Protocol-Transport Layer Security Authentication with Cisco ISE. With Cisco ISE 1.2 is it possible to enable 802.1x machine AND user smart card authentication simultaneously for wired/wireless clients (specifically Windows 7/8, but Linux or OSX would also be good).
Authentication of user using Smart card is done using authentication policy. If you want to authorize them based on AD attribute, then you need to do it in authorization policy mapping to a Shell profile/command sets. Cisco ISE Configuration. I’m using the Default Network Access allowed protocols but you can easily set it to just the protocols you require (recommended). In the default protocols, I’m enabling TEAP and EAP Chaining. Modifying the Default Network Access policy under Allowed Protocols.
This document describes how to configure Client Certificate-based authentication for Identity Services Engine (ISE) management access. In this example, the ISE administrator authenticates against the User certificate to gain Admin accessto the Cisco Identity Services Engine (ISE) management GUI.
Has anyone gotten smartcard authentication working for ISE GUI admins? I've configured this based on the Cisco documentation and the browser prompts the user to select the certificate and then enter their PIN. Cisco ISE - Configuring TACACS+ Authentication for Device Administration. Introduction. Centralizing control over network device access using the TACACS+ protocol has been the golden standard for many years in most bigger networks because it enables detailed and granular permissions down at the very command level.
sumup 3g+ payment kit smart card / nfc reader
Positive reviews gathered through NFC cards can significantly enhance your online reputation .
cisco ise smart card authentication|Cisco ise authentication error