stealing credit card numbers with rfid People often discover their credit card numbers have been stolen by receiving a transaction notification or bank statement showing an unfamiliar transaction. If your card is still with you, it’s possible someone obtained your information while you were using the card or via an RFID reader. Get all the Auburn football radio you could need, with TuneIn. You can listen to our Auburn football radio station anywhere in the country. . Auburn Tigers at Alabama Crimson Tide. 7PM. Premium Exclusive Sports. Your Pregame .
0 · rfid wallet scam
1 · rfid embedded credit cards
2 · rfid credit card security tips
3 · rfid credit card security
4 · rfid credit card scam
5 · how to protect rfid credit cards
6 · checking for rfid cards
7 · are rfid credit cards safe
The Catch II was a National Football League (NFL) Wild Card Playoff game between the Green Bay Packers and the San Francisco 49ers on January 3, 1999. The game, which was played at 3Com Park in San Francisco, California, became notable after a completed pass with 8 seconds left in the 4th quarter won the game for the 49ers. The 49ers, who had just lost the lead to the Packers late i.
rfid wallet scam
People often discover their credit card numbers have been stolen by receiving a transaction . Some security experts have voiced concerns about a phenomenon called RFID skimming, in which a thief with an RFID reader may be able to steal your credit card number or personal information simply by walking within a few feet of you.

rfid reader exe
People often discover their credit card numbers have been stolen by receiving a transaction notification or bank statement showing an unfamiliar transaction. If your card is still with you, it’s possible someone obtained your information while you were using the card or via an RFID reader. Intercepting contactless payments. With contactless payments, thieves can use radio frequency identification (RFID) technology to skim your card’s information if they’re close enough to the card reader. How to protect yourself: Use RFID-blocking wallets or cases to shield your cards from unauthorized scans. 9. Use a temporary credit card for online shopping. Many banks and credit companies will offer this service for no fee. You can get a card number that is separate from your actual account, but the bank links it to your account for your bona fide purchases.
In 2015, security researchers were able to wirelessly steal RFID credit card information (e.g., account numbers and expiration dates) from closely held, unobstructed cards and re-use them. RFID theft is a misunderstood risk associated with modern technology. While it is theoretically possible to steal someone’s card information using RFID skimmers, the data they get would be missing the necessary identifiers to carry out large scale fraud or in most cases even a simple transaction.
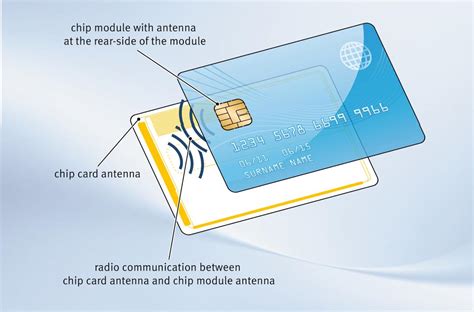
Passive Tags. Radio Frequency Identification (RFID) tags require a radio signal emitted by the receiver in order to read them. Due to this, they operate within a limited distance and are not capable of transmitting large amounts of data. Examples of RFID tags can be seen in credit cards and door passes. Active Tags. If you suspect your credit card number may be compromised, ask your card issuer for a new card. Card issuers will always issue a new card in the event of fraud (or even for a lost credit. Tips for preventing credit card theft. RFID credit cards are some of the most secure credit cards at our disposal, but it’s still good to take precautions as with any other credit.
Ways your credit card numbers can be stolen. In today’s digital-first world, your physical credit card may no longer be a hacker’s prime target. But that doesn’t mean they can’t still get their. Some security experts have voiced concerns about a phenomenon called RFID skimming, in which a thief with an RFID reader may be able to steal your credit card number or personal information simply by walking within a few feet of you.People often discover their credit card numbers have been stolen by receiving a transaction notification or bank statement showing an unfamiliar transaction. If your card is still with you, it’s possible someone obtained your information while you were using the card or via an RFID reader. Intercepting contactless payments. With contactless payments, thieves can use radio frequency identification (RFID) technology to skim your card’s information if they’re close enough to the card reader. How to protect yourself: Use RFID-blocking wallets or cases to shield your cards from unauthorized scans. 9.
Use a temporary credit card for online shopping. Many banks and credit companies will offer this service for no fee. You can get a card number that is separate from your actual account, but the bank links it to your account for your bona fide purchases. In 2015, security researchers were able to wirelessly steal RFID credit card information (e.g., account numbers and expiration dates) from closely held, unobstructed cards and re-use them. RFID theft is a misunderstood risk associated with modern technology. While it is theoretically possible to steal someone’s card information using RFID skimmers, the data they get would be missing the necessary identifiers to carry out large scale fraud or in most cases even a simple transaction. Passive Tags. Radio Frequency Identification (RFID) tags require a radio signal emitted by the receiver in order to read them. Due to this, they operate within a limited distance and are not capable of transmitting large amounts of data. Examples of RFID tags can be seen in credit cards and door passes. Active Tags.
If you suspect your credit card number may be compromised, ask your card issuer for a new card. Card issuers will always issue a new card in the event of fraud (or even for a lost credit. Tips for preventing credit card theft. RFID credit cards are some of the most secure credit cards at our disposal, but it’s still good to take precautions as with any other credit.
rfid embedded credit cards
rfid credit card security tips
rfid reader hid
rfid credit card security
The Drive with Bill Cameron, ESPN 106.7’s weekday afternoon sports show, is a fast-paced, in-depth look at the world of sports with a focus on Auburn University and local high schools. Live from 4:00 p.m.-6:00 p.m., the show has been .
stealing credit card numbers with rfid|how to protect rfid credit cards