defeat rfid tracking An MITM attack against an RFID system uses a hardware device to capture and decode the RFID signal between the victim’s card and a card reader. The malicious device then decodes the information and transmits it to the attacker so they can replay the code and gain access to the building. $16.99
0 · rfid security problems
1 · rfid security and prevention
2 · rfid hacking
3 · rfid card security attacks
4 · rfid blocking devices
5 · rfid attacks
6 · how to stop rfid hacking
7 · can rfid hackers work
Unlikely. Access control cards are likely to be either 125khz rfid (which your phone does not have the hardware to transmit at) or Mifare (which your phone's software is unable to emulate. usually). It's more likely you could clone the .Important: For users with a Pixel 7 or Pixel 7 Pro, Face Unlock is currently not supported for tap to pay transactions. Turn on your screen, then unlock your phone. You don’t need to open the Google Wallet app. Tip: In most countries or regions, smaller transactions don't require you to unlock your phone. See more
One of the easiest ways to prevent RFID hacking is to invest in badges and wallets that block RFID signals. RFID blockers prevent both scanners and legitimate readers from . Hackers can and have jammed RFID cards and tags from working simply by being nearby and generating a signal that is stronger than the one being put out by the RFID reader. .
copy smart card nfc
One of the easiest ways to prevent RFID hacking is to invest in badges and wallets that block RFID signals. RFID blockers prevent both scanners and legitimate readers from scanning your card so using it off-premises is the perfect way . An MITM attack against an RFID system uses a hardware device to capture and decode the RFID signal between the victim’s card and a card reader. The malicious device then decodes the information and transmits it to the attacker so they can replay the code and gain access to the building. Hackers can and have jammed RFID cards and tags from working simply by being nearby and generating a signal that is stronger than the one being put out by the RFID reader. This can make it impossible to track inventory using RFID, while also creating general havoc by preventing access using ID cards. Eavesdropping.
In this paper we analyze some of the most common types of attack on RFID tags: unauthorized disabling, unauthorized cloning, unauthorized tracking, and response replay. We introduce security mechanisms appropriate to defeat these attacks, and show how a recently proposed RFID authentication protocol uses them to achieve security.
can nfc card set off store alarms
Hackers using RFID scanners can theoretically steal money via your phone's tap-to-pay app. Here's how to prevent RFID hacking.To stay safe from RFID hacking, there are several steps you can take. First, use RFID blocking wallets and bags to protect your credit and debit cards from unauthorized skimming. These products create a Faraday cage that blocks RFID signals, preventing attackers from accessing your sensitive data.One such method is known as RFID cloning, where an attacker copies the information from a legitimate tag onto a counterfeit tag. By doing so, the attacker can gain unauthorized access to restricted areas or deceive systems that rely on RFID authentication.By understanding the basics of RFID technology, comprehending the threats posed by RFID hacking, and implementing robust protection strategies, organizations can safeguard their RFID systems and protect their valuable assets and sensitive information from .
choosing a card to pay with on nfc
RFID theft, also known as skimming or electronic pickpocketing, takes advantage of the vulnerabilities in RFID technology to steal personal information from RFID-enabled cards or tags. Understanding how RFID theft works is crucial .
In this paper we analyze some of the most common types of attack on RFID tags: unauthorized disabling, unauthorized cloning, unauthorized tracking, and response replay. We introduce security. One of the easiest ways to prevent RFID hacking is to invest in badges and wallets that block RFID signals. RFID blockers prevent both scanners and legitimate readers from scanning your card so using it off-premises is the perfect way . An MITM attack against an RFID system uses a hardware device to capture and decode the RFID signal between the victim’s card and a card reader. The malicious device then decodes the information and transmits it to the attacker so they can replay the code and gain access to the building. Hackers can and have jammed RFID cards and tags from working simply by being nearby and generating a signal that is stronger than the one being put out by the RFID reader. This can make it impossible to track inventory using RFID, while also creating general havoc by preventing access using ID cards. Eavesdropping.
In this paper we analyze some of the most common types of attack on RFID tags: unauthorized disabling, unauthorized cloning, unauthorized tracking, and response replay. We introduce security mechanisms appropriate to defeat these attacks, and show how a recently proposed RFID authentication protocol uses them to achieve security.
Hackers using RFID scanners can theoretically steal money via your phone's tap-to-pay app. Here's how to prevent RFID hacking.
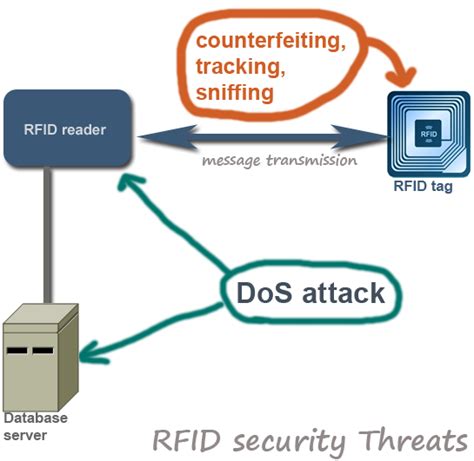
To stay safe from RFID hacking, there are several steps you can take. First, use RFID blocking wallets and bags to protect your credit and debit cards from unauthorized skimming. These products create a Faraday cage that blocks RFID signals, preventing attackers from accessing your sensitive data.One such method is known as RFID cloning, where an attacker copies the information from a legitimate tag onto a counterfeit tag. By doing so, the attacker can gain unauthorized access to restricted areas or deceive systems that rely on RFID authentication.
rfid security problems
rfid security and prevention
By understanding the basics of RFID technology, comprehending the threats posed by RFID hacking, and implementing robust protection strategies, organizations can safeguard their RFID systems and protect their valuable assets and sensitive information from . RFID theft, also known as skimming or electronic pickpocketing, takes advantage of the vulnerabilities in RFID technology to steal personal information from RFID-enabled cards or tags. Understanding how RFID theft works is crucial .
rfid hacking

check oyster card balance nfc
credit card machines with nfc
In the first half, the Buccaneers held a 242-182-yard advantage over the Eagles and a 79-17 rushing net yard advantage over Philadelphia. Coming out of the half, the Bucs' defense got a quick stop .
defeat rfid tracking|rfid attacks