smart card authentication technology It integrates a microprocessor, some memory, and some apps. The circular metal contact is vital to connect to the chip below and activate the card electrically. It's used with a contact or contactless card reader(POS for payments, at the ATM, or even on your mobile phone). Why? The card reader (or mobile phone) . See more Step 3: Place the iPhone near the RFID tag. Position your iPhone close to the RFID tag that you want to scan. Typically, the working range for NFC scanning is within a few centimeters, so ensure that you bring the iPhone and .
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
After restarting the polling sequence, the reader session sends newly detected .
It integrates a microprocessor, some memory, and some apps. The circular metal contact is vital to connect to the chip below and activate the card electrically. It's used with a contact or contactless card reader(POS for payments, at the ATM, or even on your mobile phone). Why? The card reader (or mobile phone) . See moreIn the form of credit cards and SIM cards, smart cardsare the most common form of IT processing power on the planet. It is estimated that . See moreAccording to Markets and Markets' recent research report, the smart card marketvalueis expected to reach .9 billion by 2026. . See moreAccording to the 11 February 2023Eurosmartforecasts, smart card markets will probably exceed 10 billion units in 2022. The . See more
Roland Moreno patented the memory card in 1974. By 1977, three commercial manufacturers, Bull CP8, SGS Thomson, and Schlumberger, started developing smart card products. In March 1979, Michel Hugon from Bull CP8 was the first to design and . See moreHow Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
As a National eID card, smart health card, residence permit, or electronic passport, smart card technology offers more robust identification and authentication tools for both authorities' and .How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
smart card multi factor authentication
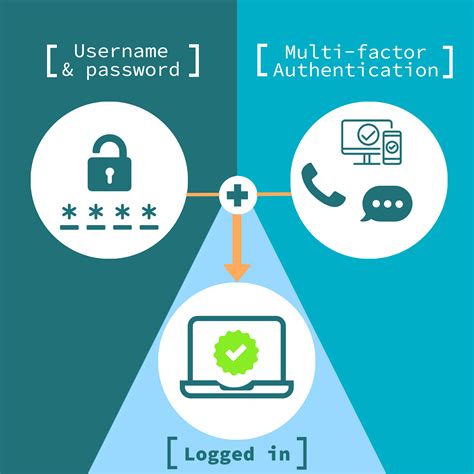
Smart cards serve as credit or ATM cards, fuel cards, mobile phone SIMs, authorization cards for pay television, household utility pre-payment cards, high-security identification and access . Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in . Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, .
This article describes the virtual smart card technology and how it can fit into your authentication design. Virtual smart card technology uses cryptographic keys that are stored .
Smart Card Authentication is a means of verifying users into enterprise resources using a physical card in tandem with a smart card reader and software.Smart card authentication is a security technology that uses smart cards, which are small plastic cards with embedded microchips, to prove a user's identity. The microchip securely stores the . Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data .The Smart Card Alliance is a not-for-profit, multi-industry association working to stimulate the understanding, adoption, use and widespread application of smart card technology.
As a National eID card, smart health card, residence permit, or electronic passport, smart card technology offers more robust identification and authentication tools for both authorities' and .How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.Smart cards serve as credit or ATM cards, fuel cards, mobile phone SIMs, authorization cards for pay television, household utility pre-payment cards, high-security identification and access .
Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in . Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, . This article describes the virtual smart card technology and how it can fit into your authentication design. Virtual smart card technology uses cryptographic keys that are stored .
Smart Card Authentication is a means of verifying users into enterprise resources using a physical card in tandem with a smart card reader and software.
Smart card authentication is a security technology that uses smart cards, which are small plastic cards with embedded microchips, to prove a user's identity. The microchip securely stores the .
Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data .
smart card identity

rfid poker chip
smart card based identification system
Reading an NFC tag on your iPhone is quite simple. On newer models that have a passive NFC reader, all you need to do is bring your iPhone . See more
smart card authentication technology|smart card authentication step by