linux ssh smart card Smart Card Logon for SSH For network engineers, this guide will help you authenticate with your PIV/CAC credential and use SSH to access a remote Linux server from a Windows or macOS . The NFL playoffs' wild-card round schedule for the 2024 season is stacked with great matchups, and we've got you covered with what you need to know heading into the .Detroit Lions 20 at Dallas Cowboys 24 on January 4th, 2015 - Full team and player stats and box score . Wild Card - Detroit Lions at Dallas Cowboys - January 4th, 2015. via Sports .
0 · Smart card authentication with SSH
1 · Smart card authentication
2 · Smart Card Logon for SSH
3 · Smart
4 · Managing smart card authentication
5 · How to Set up SmartCard Authentication on Linux
6 · How can I set up smart card SSH authentication?
7 · Chapter 6. Configuring smart card authentication with local
8 · About SSH and Smart Card support (RHEL 7)
You can try NFC Tools or the MiFare Classic Tool to emulate cards from your phone, but in my .Seattle Seahawks 22 at Dallas Cowboys 24 on January 5th, 2019 - Full team and player stats and box score . 2018 NFL Scores & Schedule; Dallas Cowboys Schedule; Seattle Seahawks .
Most of the cards are read-only and do not need this step. If your card is issued by the third party (a government), you already have pre-generated keys and . See moreConnecting using public key in SSH requires the presence of the public key on the server to verify clients signatures. If we don't have the public key stored . See moreOne of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner .Smart Card Logon for SSH For network engineers, this guide will help you authenticate with your PIV/CAC credential and use SSH to access a remote Linux server from a Windows or macOS .
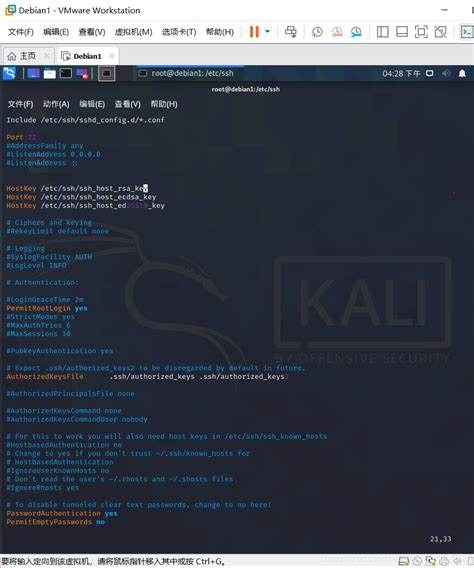
Use this method to enforce SSH smart card login on a per user basis. After this step you can SSH into the server using the smart card for authentication.To enable smart card authentication we should rely on a module that allows PAM supported systems to use X.509 certificates to authenticate logins. The module relies on a PKCS#11 .One of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner .In Red Hat Enterprise Linux, we strive to support several popular smart-card types. However, because it is not possible to support every smart card available, this document specifies our .
If you are using your smart card to authenticate using SSH, you need to add the full certificate to the user entry in Identity Management (IdM). If you are not using your smart card to .To configure smart card authentication with local certificates: The host is not connected to a domain. You want to authenticate with a smart card on this host. You want to configure SSH . It can be used to configure smart card authentication on a Linux system by using the "smartcard" auth provider. And configure PAM (Pluggable Authentication Modules) to use .This article describes the supported way of setting up and using smart cards for authentication in Secure Shell for Red Hat Enterprise Linux 7.
Smart card authentication with SSH
One of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner of the corresponding private key in the smart card can then SSH login to the server.
Smart Card Logon for SSH For network engineers, this guide will help you authenticate with your PIV/CAC credential and use SSH to access a remote Linux server from a Windows or macOS computer. For server administrators, this guide will help you configure a . Use this method to enforce SSH smart card login on a per user basis. After this step you can SSH into the server using the smart card for authentication.
To enable smart card authentication we should rely on a module that allows PAM supported systems to use X.509 certificates to authenticate logins. The module relies on a PKCS#11 library, such as opensc-pkcs11 to access the smart card for the credentials it will need.One of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner of the corresponding private key in the smart card can then SSH login to the server.In Red Hat Enterprise Linux, we strive to support several popular smart-card types. However, because it is not possible to support every smart card available, this document specifies our targeted cards.If you are using your smart card to authenticate using SSH, you need to add the full certificate to the user entry in Identity Management (IdM). If you are not using your smart card to authenticate using SSH, you can add certificate mapping data using the ipa user-add-certmapdata command.
Smart card authentication
To configure smart card authentication with local certificates: The host is not connected to a domain. You want to authenticate with a smart card on this host. You want to configure SSH access using smart card authentication. You want to configure the smart card with authselect.
It can be used to configure smart card authentication on a Linux system by using the "smartcard" auth provider. And configure PAM (Pluggable Authentication Modules) to use SSSD for smart card authentication.This article describes the supported way of setting up and using smart cards for authentication in Secure Shell for Red Hat Enterprise Linux 7.
smart real nid card
One of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner of the corresponding private key in the smart card can then SSH login to the server.Smart Card Logon for SSH For network engineers, this guide will help you authenticate with your PIV/CAC credential and use SSH to access a remote Linux server from a Windows or macOS computer. For server administrators, this guide will help you configure a .
Use this method to enforce SSH smart card login on a per user basis. After this step you can SSH into the server using the smart card for authentication.To enable smart card authentication we should rely on a module that allows PAM supported systems to use X.509 certificates to authenticate logins. The module relies on a PKCS#11 library, such as opensc-pkcs11 to access the smart card for the credentials it will need.One of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner of the corresponding private key in the smart card can then SSH login to the server.
In Red Hat Enterprise Linux, we strive to support several popular smart-card types. However, because it is not possible to support every smart card available, this document specifies our targeted cards.If you are using your smart card to authenticate using SSH, you need to add the full certificate to the user entry in Identity Management (IdM). If you are not using your smart card to authenticate using SSH, you can add certificate mapping data using the ipa user-add-certmapdata command.To configure smart card authentication with local certificates: The host is not connected to a domain. You want to authenticate with a smart card on this host. You want to configure SSH access using smart card authentication. You want to configure the smart card with authselect.
Smart Card Logon for SSH
Smart
Managing smart card authentication
How to Set up SmartCard Authentication on Linux

About Credit Card Reader NFC (EMV) 5.5.1. This app was designed to allow .
linux ssh smart card|How to Set up SmartCard Authentication on Linux