smart card authentication software How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. $23.00
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
Access the Copied RFID Card: After saving the RFID card’s data to your iPhone, you can now access the copied card within the NFC writer app whenever needed. Select the copied card from the app to utilize its .If you prefer a non-jailbreak method, you can copy an NFC card to your iPhone using a third-party app specifically designed for NFC copying. Follow these steps to copy an .
EIDAuthenticate is the solution to perform smart card authentication on stand alone computers or to protect local accounts on domain computers.
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
EIDAuthenticate is the solution to perform smart card authentication on stand alone computers or to protect local accounts on domain computers.Smart card-based public key infrastructure (PKI) authentication for Windows login, VPN, Login, Remote Sessions, as well as data security, digital signature and secure email. Two-factor authentication with one-time passwords (OTP) when deployed with ActivID AAA Server for Remote Access or ActivID Appliance. Virtual smart cards are a technology from Microsoft that offers comparable security benefits in two-factor authentication to physical smart cards. They also offer more convenience for users and lower cost for organizations to deploy. Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers.
smart card multi factor authentication
Thales' smart cards offer a single solution for strong authentication and applications access control, including remote access, network access, password management, network logon, as well as corporate ID badges, magnetic stripes and proximity.
Whether you choose to deploy on-premise or in the cloud, HID provides the industry’s broadest range of authentication methods and form factors, including smart cards and security keys with support for FIDO, PKI, OATH and more. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.Smart card authentication FAQs. What is smart card authentication? Smart card authentication is a security technology that uses smart cards, which are small plastic cards with embedded microchips, to prove a user's identity.
smart card identity
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
EIDAuthenticate is the solution to perform smart card authentication on stand alone computers or to protect local accounts on domain computers.Smart card-based public key infrastructure (PKI) authentication for Windows login, VPN, Login, Remote Sessions, as well as data security, digital signature and secure email. Two-factor authentication with one-time passwords (OTP) when deployed with ActivID AAA Server for Remote Access or ActivID Appliance. Virtual smart cards are a technology from Microsoft that offers comparable security benefits in two-factor authentication to physical smart cards. They also offer more convenience for users and lower cost for organizations to deploy. Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers.
smart card based identification system
Thales' smart cards offer a single solution for strong authentication and applications access control, including remote access, network access, password management, network logon, as well as corporate ID badges, magnetic stripes and proximity.Whether you choose to deploy on-premise or in the cloud, HID provides the industry’s broadest range of authentication methods and form factors, including smart cards and security keys with support for FIDO, PKI, OATH and more.
Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.
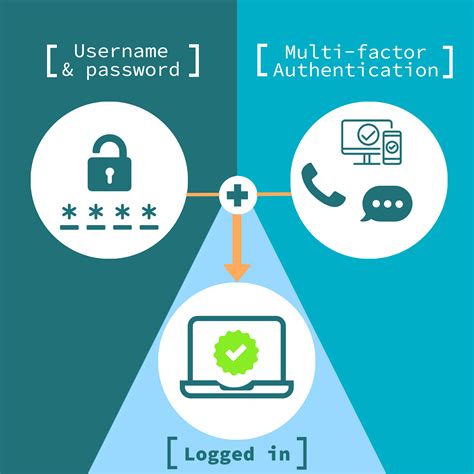
smart card authentication step by

smart card authentication protocol
enable smart card log on
Get NFC Reader old version APK for Android. Download. Über NFC Reader. .
smart card authentication software|authenticate using your smart card