how to secure rfid tags coded with sensitive info Eavesdropping is a technique used by attackers to intercept and decode the radio signals exchanged between RFID tags and readers. By capturing these signals, hackers can gain unauthorized access to sensitive information, such as personal identification numbers or confidential data.
$6.89
0 · two types of rfid tags
1 · rfid tags and their uses
2 · rfid radio frequency identification tags
3 · rfid privacy and security issues
4 · retail anti theft security tags
5 · radio frequency identification tags are
6 · problems with rfid technology
7 · problems with rfid
The ChameleonMini is a tool that allows you to emulate and clone high-frequency contactless cards and read RFID tags. It functions as an NFC emulator and RFID reader and can sniff and log radio .If your debit card has an NFC chip on it (the "tap to pay"), it's possible. This presentation discusses two methods. One is skimming an NFC card and using the recovered data for making Card Not Present transactions .
Encrypt RFID Data: Encrypting the data transmitted between tags and readers can protect . So how can you protect your sensitive data from falling into the wrong hands? In this article, we’ll discuss how uninvited parties might try to get ahold of your information and eight different ways you can prevent that from happening.
Encrypt RFID Data: Encrypting the data transmitted between tags and readers can protect sensitive information from unauthorized access. Enable Authentication: Implement authentication mechanisms to ensure that only authorized tags and readers can interact with each other. By closely monitoring the power consumption levels of RFID tags, hackers can fool your systems. With some ingenuity and a cell phone bad actors can perform an RFID hack that will steal sensitive information or breach secured areas.
Double-Check Your RFID Security. You can also ensure your security plan does not rely on RFID only. For instance, contact your credit card issuer and see if they will disable RFID-only purchases on your card. Then if someone were to clone the RFID tag in your card you would still be safe from theft.Eavesdropping is a technique used by attackers to intercept and decode the radio signals exchanged between RFID tags and readers. By capturing these signals, hackers can gain unauthorized access to sensitive information, such as personal identification numbers or confidential data. Some QR code pet tag technology even offers security features, such as password protection, ensuring that sensitive information stays private. This innovative approach not only enhances the chances of a swift reunion but also provides peace of mind for pet owners, knowing their beloved companions are just a scan away from being safely returned .Here are the 5 best ways to secure the customer or asset related data stored in the tags. Data Maintenance. Regularly deleting unnecessary data and fine-tuning data reading settings are pivotal steps to safeguard valuable information stored in RFID tags. By periodically reviewing and removing redundant or obsolete data, you ensure that only .
By incorporating elements such as passwords, biometrics, smart cards, or one-time passcodes, MFA ensures that only authenticated personnel with the correct combination of credentials can access sensitive RFID data.
One of the most basic and effective ways to secure your RFID tags is to encrypt the data they transmit and store. Encryption scrambles the data into a code that only authorized parties can .
Implement robust encryption algorithms to secure data transmitted between RFID tags and readers. Additionally, use authentication mechanisms to ensure only authorized devices and users can access the RFID system. So how can you protect your sensitive data from falling into the wrong hands? In this article, we’ll discuss how uninvited parties might try to get ahold of your information and eight different ways you can prevent that from happening.Encrypt RFID Data: Encrypting the data transmitted between tags and readers can protect sensitive information from unauthorized access. Enable Authentication: Implement authentication mechanisms to ensure that only authorized tags and readers can interact with each other. By closely monitoring the power consumption levels of RFID tags, hackers can fool your systems. With some ingenuity and a cell phone bad actors can perform an RFID hack that will steal sensitive information or breach secured areas.
Double-Check Your RFID Security. You can also ensure your security plan does not rely on RFID only. For instance, contact your credit card issuer and see if they will disable RFID-only purchases on your card. Then if someone were to clone the RFID tag in your card you would still be safe from theft.Eavesdropping is a technique used by attackers to intercept and decode the radio signals exchanged between RFID tags and readers. By capturing these signals, hackers can gain unauthorized access to sensitive information, such as personal identification numbers or confidential data. Some QR code pet tag technology even offers security features, such as password protection, ensuring that sensitive information stays private. This innovative approach not only enhances the chances of a swift reunion but also provides peace of mind for pet owners, knowing their beloved companions are just a scan away from being safely returned .Here are the 5 best ways to secure the customer or asset related data stored in the tags. Data Maintenance. Regularly deleting unnecessary data and fine-tuning data reading settings are pivotal steps to safeguard valuable information stored in RFID tags. By periodically reviewing and removing redundant or obsolete data, you ensure that only .
By incorporating elements such as passwords, biometrics, smart cards, or one-time passcodes, MFA ensures that only authenticated personnel with the correct combination of credentials can access sensitive RFID data. One of the most basic and effective ways to secure your RFID tags is to encrypt the data they transmit and store. Encryption scrambles the data into a code that only authorized parties can .

two types of rfid tags
rfid tags and their uses

rfid radio frequency identification tags
rfid privacy and security issues
retail anti theft security tags
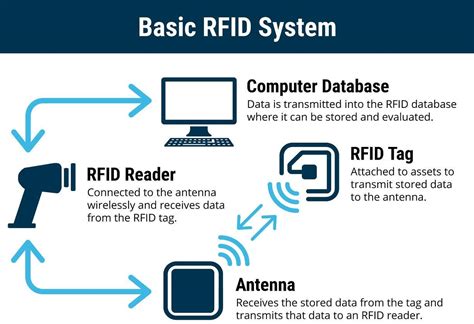
6. Assuming the RFID system you are talking about only expects a key, and then .It's just a NFC tag in a card instead of a figure. There is absolutely no problem in using them. I don't think they are even able to damage your switch. I got 22 of these cards for BotW. Had no problems. Used it also on the switch of a friend. Also no problems.
how to secure rfid tags coded with sensitive info|two types of rfid tags