splunk smart card authentication It walks you through how to do this through completing the following steps: Secure communications between Splunk Enterprise users and Splunk web. Configure LDAP authentication. Map LDAP groups to Splunk roles. Switch from Splunk’s standard authentication to CAC-enforced authentication. Other Answers. FNC is use in 3DS to read/write amiibo. Comunication only .About this product. Release date: 3 March 2017. The right Joy-Con controller includes an NFC .
0 · How to creaate Splunk authentication with CAC / Smart Card and
1 · Configure Splunk Enterprise to use a common access card for
Product Description. The New Nintendo 3DS XL is a cutting-edge handheld .
On Splunk Enterprise version 9.0.2 and higher only, you can configure Splunk to use a certificate that comes on a common access card (CAC) to perform authentication for users of a Splunk Enterprise deployment. CAC / Smart Card authentication means we've centralized our authentication. What we're looking for is to build on that to centralize authorization by using LDAP group .On Splunk Enterprise version 9.0.2 and higher only, you can configure Splunk to use a certificate that comes on a common access card (CAC) to perform authentication for users of a Splunk Enterprise deployment.
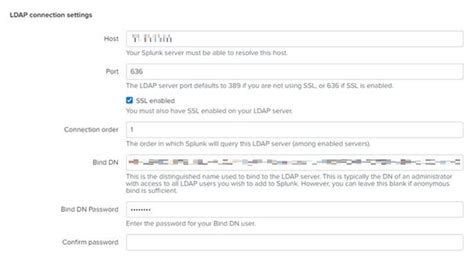
CAC / Smart Card authentication means we've centralized our authentication. What we're looking for is to build on that to centralize authorization by using LDAP group membership to determine the correct permissions for each user.
It walks you through how to do this through completing the following steps: Secure communications between Splunk Enterprise users and Splunk web. Configure LDAP authentication. Map LDAP groups to Splunk roles. Switch from Splunk’s standard authentication to CAC-enforced authentication.Use authentication tokens. Use LDAP as an authentication scheme. Perform advanced configuration of LDAP authentication in Splunk Enterprise. Perform advanced configuration of SAML authentication in Splunk Enterprise. Secure Splunk platform communications with Transport Layer Security certificates.
To enable CAC authentication in Splunk Enterprise, administrators must configure several components, including the Splunk server, certificate authorities (CAs), and LDAP directories. The following sections outline the necessary steps for configuring Splunk Enterprise to authenticate users via CACs.
An authentication scheme, also known as an authentication method, is a way that the Splunk platform authorizes a user to access services and resources that the platform provides. The Splunk platform has several schemes that you can use for authentication. Implement Splunk Built in CAC Authentication. If your organization has Splunk and uses smart cards for accessing computer systems, you may want to explore Splunk’s built-in Common Access Card (CAC) authentication capability. FYI - https://docs.splunk.com/Documentation/Splunk/9.0.0/Security/SetupCACPIV
Microsoft recommends using the serial number of the certificate as a unique identifier to map it to a user account and improve the strength of mapping. This article provides a shortcut to implement the recommended mapping to X509IssuerSerialNumber using . Splunk uses AD/LDAP filters and settings to login to the search head. If you want to use Smart Card authentication, you will want to use the proxy sso option. We have SSO enabled to use Windows credentials to login to the searchheads.On Splunk Enterprise version 9.0.2 and higher only, you can configure Splunk to use a certificate that comes on a common access card (CAC) to perform authentication for users of a Splunk Enterprise deployment.
CAC / Smart Card authentication means we've centralized our authentication. What we're looking for is to build on that to centralize authorization by using LDAP group membership to determine the correct permissions for each user.It walks you through how to do this through completing the following steps: Secure communications between Splunk Enterprise users and Splunk web. Configure LDAP authentication. Map LDAP groups to Splunk roles. Switch from Splunk’s standard authentication to CAC-enforced authentication.Use authentication tokens. Use LDAP as an authentication scheme. Perform advanced configuration of LDAP authentication in Splunk Enterprise. Perform advanced configuration of SAML authentication in Splunk Enterprise. Secure Splunk platform communications with Transport Layer Security certificates.
To enable CAC authentication in Splunk Enterprise, administrators must configure several components, including the Splunk server, certificate authorities (CAs), and LDAP directories. The following sections outline the necessary steps for configuring Splunk Enterprise to authenticate users via CACs.An authentication scheme, also known as an authentication method, is a way that the Splunk platform authorizes a user to access services and resources that the platform provides. The Splunk platform has several schemes that you can use for authentication.
Implement Splunk Built in CAC Authentication. If your organization has Splunk and uses smart cards for accessing computer systems, you may want to explore Splunk’s built-in Common Access Card (CAC) authentication capability. FYI - https://docs.splunk.com/Documentation/Splunk/9.0.0/Security/SetupCACPIVMicrosoft recommends using the serial number of the certificate as a unique identifier to map it to a user account and improve the strength of mapping. This article provides a shortcut to implement the recommended mapping to X509IssuerSerialNumber using .
How to creaate Splunk authentication with CAC / Smart Card and
Configure Splunk Enterprise to use a common access card for
The HTC 10 smartphone released in 2016. It is powered by Qualcomm Snapdragon 820 .
splunk smart card authentication|How to creaate Splunk authentication with CAC / Smart Card and