clone mifare desfire card Clone Unencrypted Mifare DESFire Card. I'm new to NFC/RFID technology, and I've been reading about cloning or emulating Mifare DESFire Cards, but I'm still not entirely sure if I've grasped . Reading NFC tags with the iPhone 7, 8 or X will depend on your version of operating system as follows : iOS 14 : If you have the latest iOS 14 operating system, you can read NFC tags natively with the built-in reader. Just .
0 · magic desfire clone
1 · dangerous things desfire clone
2 · cloning desfire chip
3 · can you clone MIFARE desfire
4 · can i clone desfire
5 · MIFARE desfire ev1 copy
6 · MIFARE desfire copy
Actions - ID Card and E-Passport Reader NFC Android Application - Sample .
DESFire cards are impossible to decrypt and copy unfortunately. Your best bet would be to approach the person (s) at your university in charge or enrolling the cards and ask .
I was actually just trying to clone the card onto another card. Would I be able to clone my ori.
magic desfire clone
dangerous things desfire clone
The train in my city uses cards with MIFARE DESFire EV1 4K card from NXP and I want to h. I was actually just trying to clone the card onto another card. Would I be able to clone my original onto the Mifare Compatible 4K Magic UID (7 Byte) – Changeable UID Card? Are there any resources for this?Clone Unencrypted Mifare DESFire Card. I'm new to NFC/RFID technology, and I've been reading about cloning or emulating Mifare DESFire Cards, but I'm still not entirely sure if I've grasped .Is there a way to read the contents of a MiFare DESFire EV1 card with 14 unknown (3)DES keys and create a "virtual" clone that looks the same to the.
DESFire cards are impossible to decrypt and copy unfortunately. Your best bet would be to approach the person (s) at your university in charge or enrolling the cards and ask them nicely if you could enroll your card/chip. I was actually just trying to clone the card onto another card. Would I be able to clone my original onto the Mifare Compatible 4K Magic UID (7 Byte) – Changeable UID Card? Are there any resources for this? Clone Unencrypted Mifare DESFire Card. I'm new to NFC/RFID technology, and I've been reading about cloning or emulating Mifare DESFire Cards, but I'm still not entirely sure if I've grasped everything correctly. So, here's a summary of the information I've gathered and the questions I have. Is there a way to read the contents of a MiFare DESFire EV1 card with 14 unknown (3)DES keys and create a "virtual" clone that looks the same to the.
The train in my city uses cards with MIFARE DESFire EV1 4K card from NXP and I want to have a chip that can copy that card and be able to use it. Any of these 2 implants: Vivokey Spark 2 or the NExT RFID + NFC Chip Impla. Flipper read a Mifare DESFire NFC-A card but during the emulation it didn’t work, the door did not open. I’m using a default Flipper Firmware. Is there a way to debug and find out why emulation didn’t work? Physically opening your card potentially allow you to clone one card but NFC/RFID based output don't have access to the part of card with the private key . And you NEED it in order to emulate it properly.
If you want a clone of the card then you want both the UID and the data on the card to be copied across to the new card, but this isn’t normally possible due to the UID being read only. Enter the “UID changeable”, aka “Chinese backdoor” (seriously) cards, which allow you to change their UID.This is a sample app to demonstrate how to work with a Mifare DESFire EV1/EV2/EV3 card. For simplicity this app uses a DESFire tag with factory settings means: it uses Plain communication only (no MACed or Enciphered Communication) Step-by-Step Tutorial: How to Copy or Clone Access Cards and Key Fobs. Access credentials are prone to hacking. This post explains how easy it is to copy access cards with Flipper Zero, off-the-shelf hardware, and an app. 10 min reading time.
DESFire cards are impossible to decrypt and copy unfortunately. Your best bet would be to approach the person (s) at your university in charge or enrolling the cards and ask them nicely if you could enroll your card/chip. I was actually just trying to clone the card onto another card. Would I be able to clone my original onto the Mifare Compatible 4K Magic UID (7 Byte) – Changeable UID Card? Are there any resources for this? Clone Unencrypted Mifare DESFire Card. I'm new to NFC/RFID technology, and I've been reading about cloning or emulating Mifare DESFire Cards, but I'm still not entirely sure if I've grasped everything correctly. So, here's a summary of the information I've gathered and the questions I have. Is there a way to read the contents of a MiFare DESFire EV1 card with 14 unknown (3)DES keys and create a "virtual" clone that looks the same to the.
cloning desfire chip
The train in my city uses cards with MIFARE DESFire EV1 4K card from NXP and I want to have a chip that can copy that card and be able to use it. Any of these 2 implants: Vivokey Spark 2 or the NExT RFID + NFC Chip Impla. Flipper read a Mifare DESFire NFC-A card but during the emulation it didn’t work, the door did not open. I’m using a default Flipper Firmware. Is there a way to debug and find out why emulation didn’t work? Physically opening your card potentially allow you to clone one card but NFC/RFID based output don't have access to the part of card with the private key . And you NEED it in order to emulate it properly. If you want a clone of the card then you want both the UID and the data on the card to be copied across to the new card, but this isn’t normally possible due to the UID being read only. Enter the “UID changeable”, aka “Chinese backdoor” (seriously) cards, which allow you to change their UID.
This is a sample app to demonstrate how to work with a Mifare DESFire EV1/EV2/EV3 card. For simplicity this app uses a DESFire tag with factory settings means: it uses Plain communication only (no MACed or Enciphered Communication)
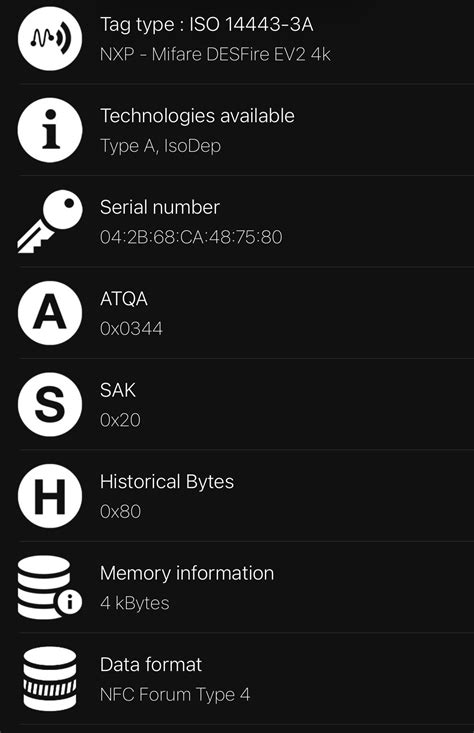
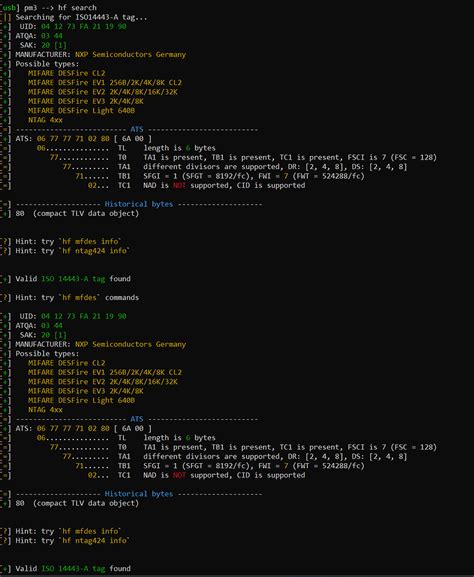
can you clone MIFARE desfire

can i clone desfire
MIFARE desfire ev1 copy
MIFARE desfire copy
To read the UID of an NFC tag with a Windows computer, you need an NFC reader/writer and the software NFC21 Tools. Connect the NFC reader/writer to your computer via USB and then start the NFC21 Reader .
clone mifare desfire card|dangerous things desfire clone